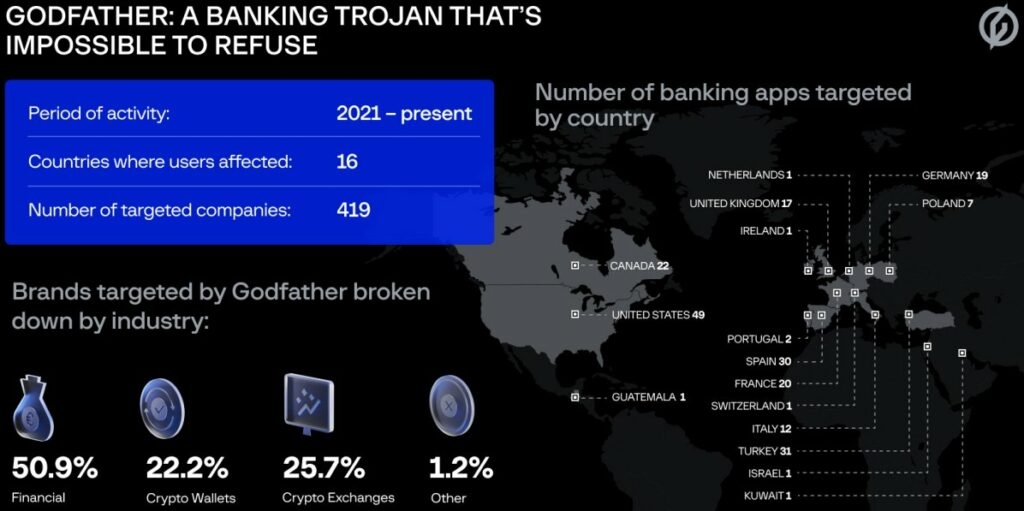
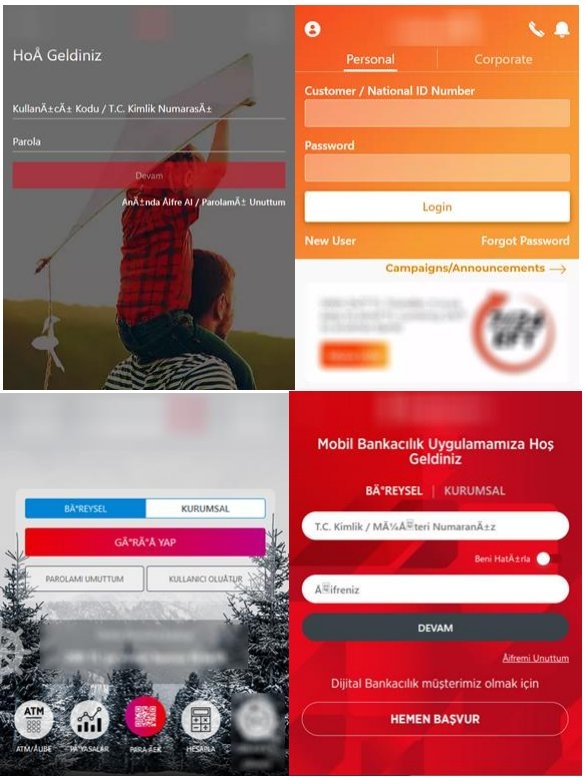
The researchers believe that the Godfather could be the replacement of the Anubis; well Anubis was a banking trojan Android malware that was widely used, although, in the end, it wasn’t used due to its inability to bypass newer Android defenses. The Android malware, i.e., Godfather, creates a login display on the top of the banking & cryptocurrency exchange app login page when the victim tries to login into the website, deceiving the targets into entering the correct credentials on the well-made HTML phishing pages. The Android malware was first discovered in March 2021 by Threat Fabric, and since then, it has seen some significant improvements & upgrades in its code. Also, a report from Cyble mentions that there’s a rise in activities of Android malware and is driving an app that impersonates a famous music tool in Turkey and has been downloaded 10 million times on Google Play Store. Well, researchers were able to find a small distribution of the Godfather malware in the apps on the Google Play Store. However, the researchers are yet to find the primary distribution mode, so the initial infection method is majorly unknown. The Android malware-targeted apps are mostly banking apps from the United States, Turkey, Canada, France, Germany, Spain, and the United Kingdom. Also, target cryptocurrency exchange platforms and cryptocurrency wallet apps. Furthermore, the trojan is set to check the system language, and if it is Russian, Armenian, Kazakh, Kyrgyz, Moldovan, Uzbek, etc., then it stops functioning. This indicates the people behind Godfather trojan speak Russian and are probably residents of the Commonwealth Independent State) Region. Well, as the trojan is installed on the device, then it mimics the Google Play Protect, a standard security check available on all Android devices. The malware goes one step further and emulates a scanning process on the handset. The objective of the scanning is to request Accessibility services that look like an authentic tool, and once the target approves the request, then the malware can give itself all the permissions to carry out all the malicious activities. The malicious activities include access to notifications and Messages, contacts, making phone calls, writing to external storage, and reading the handset status. Read: Threat Actor Targets Telecom Service Providers and Alters Defensive Methods When Detected Now, Accessibility services are exploited to prevent the victim from removing the malware and also filtrate the Google Authenticator code (OTPs), stealing the passwords & pins and processing the commands. The Android malware exfiltrates the list of apps to receive matching (Fake HTML logins to steal the credentials) from the C2 server. The web fake mimics the login pages for legitimate applications, and all the data entered into the fake HTML pages, such as usernames and passwords, is then exfiltrated to C&C servers, said the Threat Fabric researchers. In addition to this, the malware can send fake notifications from the infected apps on the victim’s handset, so it does not have to wait for the infected app to open and the apps which aren’t on the Godfather lists, the Android malware uses its screen recording feature to record the credentials that the victim enters in the fields. Moreover, the Godfather also accepts the following commands from the C2 server, which it performs through the administrative benefit it has on the device. The Android malware also features components that enable it to execute actions like keylogging, recording the screen, turning on the silent mode, starting a VNC server, locking the display, and exfiltrating and blocking notifications. As mentioned above, Godfather malware could be the creation of the same attackers that created the Anubis trojan, whose source code leaked in 2019, or this malware could consist of an entirely new threat to attackers. Well, both malware adopts similar methods of receiving the C2 address, execution of C2 commands, the fake web method, the proxy mode, etc. With that being said, the trojan excludes the Anubis file encryption, GPS tracking, etc., but rather includes the VNC server method, screen recording method, added a process to steal Google Authenticator, and more. Read: Muddy Water, a Hacker Group Used Compromised Corporate Emails for Sending Phishing Messages